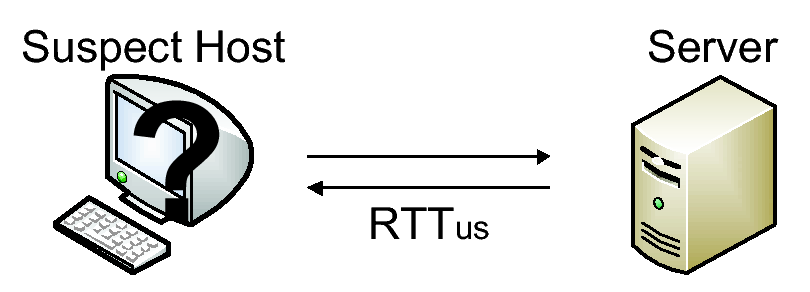
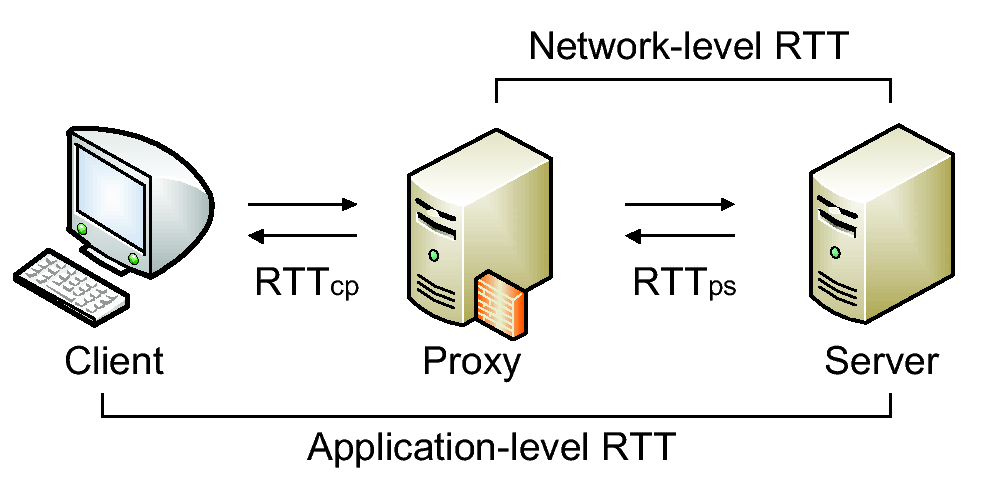
[1]
[Online]. Available:
http://en.wikipedia.org/wiki/Freegate
[2]
M. Abu Rajab, J. Zarfoss, F. Monrose, and A. Terzis, "A multifaceted approach
to understanding the botnet phenomenon," ser. IMC '06. ACM, 2006.
[3]
M. F. Arlitt, R. Friedrich, and T. Jin, "Performance evaluation of web proxy
cache replacement policies," in
Proceedings of the 10th International
Conference on Computer Performance Evaluation: Modelling Techniques and
Tools, ser. TOOLS '98.
Springer-Verlag, 1998.
[4]
A. Blum, D. Song, and S. Venkataraman, "Detection of interactive stepping
stones: Algorithms and confidence bounds," in
in Conference of Recent
Advance in Intrusion Detection (RAID), (Sophia Antipolis, French
Riviera. Springer, 2004, pp.
258-277.
[5]
R. Cáceres, F. Douglis, A. Feldmann, G. Glass, and M. Rabinovich, "Web
proxy caching: the devil is in the details,"
SIGMETRICS Perform. Eval.
Rev., vol. 26, December 1998.
[6]
N. I. Cert/cc and A. H. Cert/cc, "Botnets as a vehicle for online crime,"
2005.
[7]
B. Chun, D. Culler, T. Roscoe, A. Bavier, L. Peterson, M. Wawrzoniak, and
M. Bowman, "Planetlab: an overlay testbed for broad-coverage services,"
SIGCOMM Comput. Commun. Rev., July 2003.
[8]
R. Dingledine, N. Mathewson, and P. Syverson, "Tor: the second-generation
onion router," in
Proceedings of the 13th conference on USENIX
Security Symposium - Volume 13, ser. SSYM'04. USENIX Association, 2004.
[9]
E. Gabber, P. B. Gibbons, Y. Matias, and A. J. Mayer.
[10]
N. Hopper, E. Y. Vasserman, and E. Chan-tin, "How much anonymity does network
latency leak," in
In CCS íŽ07: Proceedings of the 14th ACM conference
on Computer and communications security. ACM, 2007.
[11]
H. Jiang and C. Dovrolis, "Passive estimation of TCP round-trip times,"
SIGCOMM Comput. Commun. Rev., July 2002.
[12]
J. C. Mogul and G. Minshall, "Rethinking the tcp nagle algorithm,"
SIGCOMM Comput. Commun. Rev., January 2001.
[13]
V. S. Pai, L. Wang, K. Park, R. Pang, and L. Peterson, "The dark side of the
web: an open proxy's view,"
SIGCOMM Comput. Commun. Rev., January
2004.
[14]
Y. Zhang and V. Paxson, "Detecting stepping stones," in
In Proceedings
of the 9th USENIX Security Symposium, 2000, pp. 171-184.
[15]
Z. Zhu, G. Lu, Y. Chen, Z. J. Fu, P. Roberts, and K. Han, "Botnet research
survey," in
Proceedings of the 32nd Annual IEEE International Computer
Software and Applications Conference, Washington, DC, USA, 2008.

 (a) Nagle's algorithm disabled
(a) Nagle's algorithm disabled
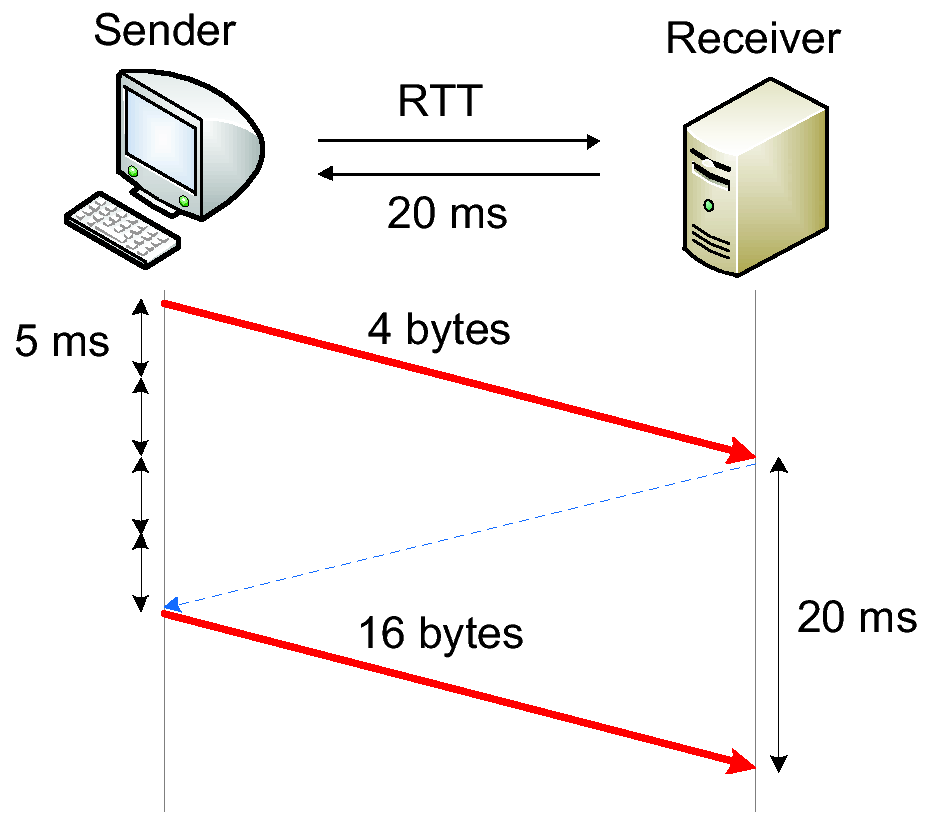 (b) Nagle's algorithm enabled
(b) Nagle's algorithm enabled
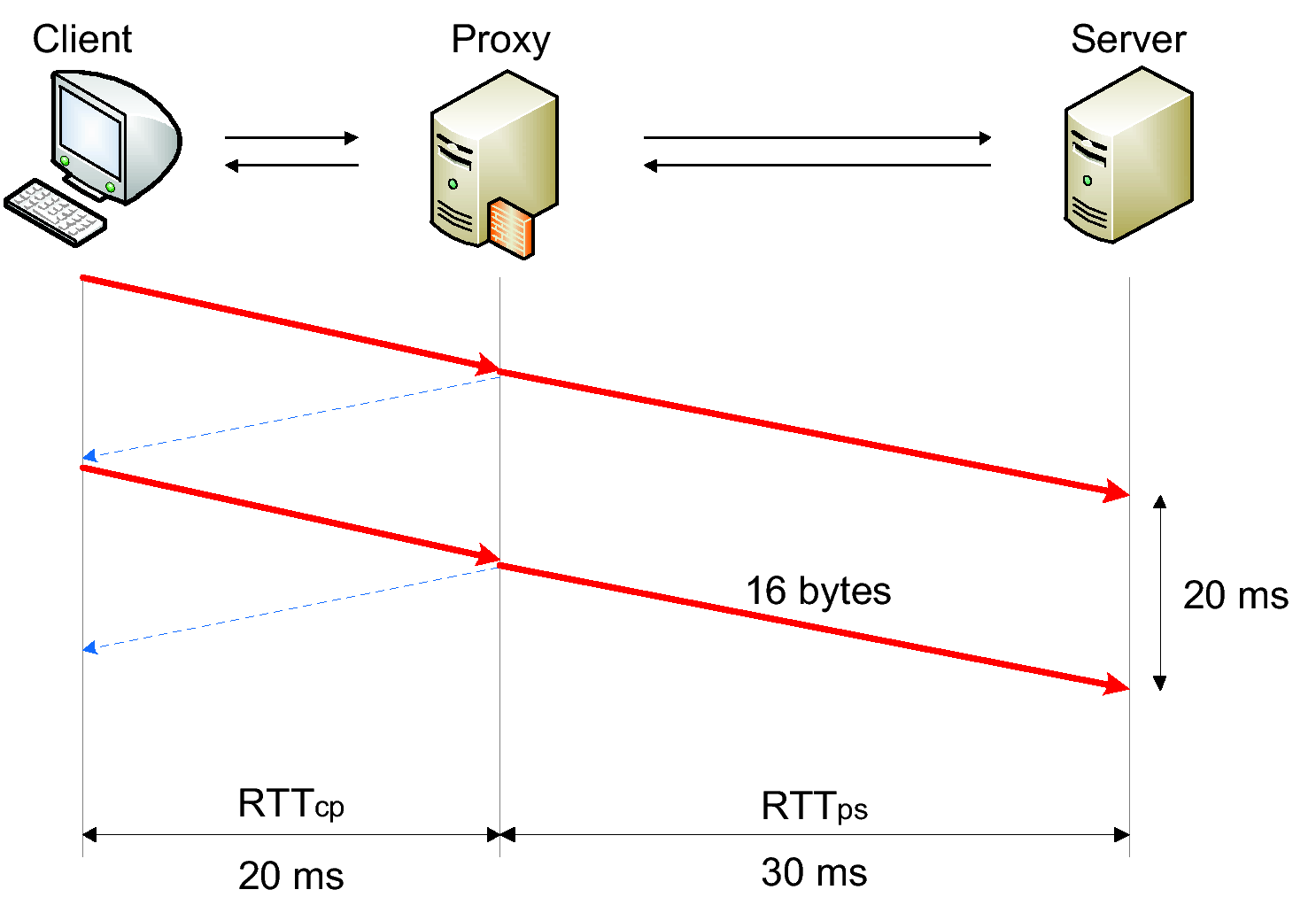 (a) Nagle-disabled proxy with RTTcp < RTTps
(a) Nagle-disabled proxy with RTTcp < RTTps
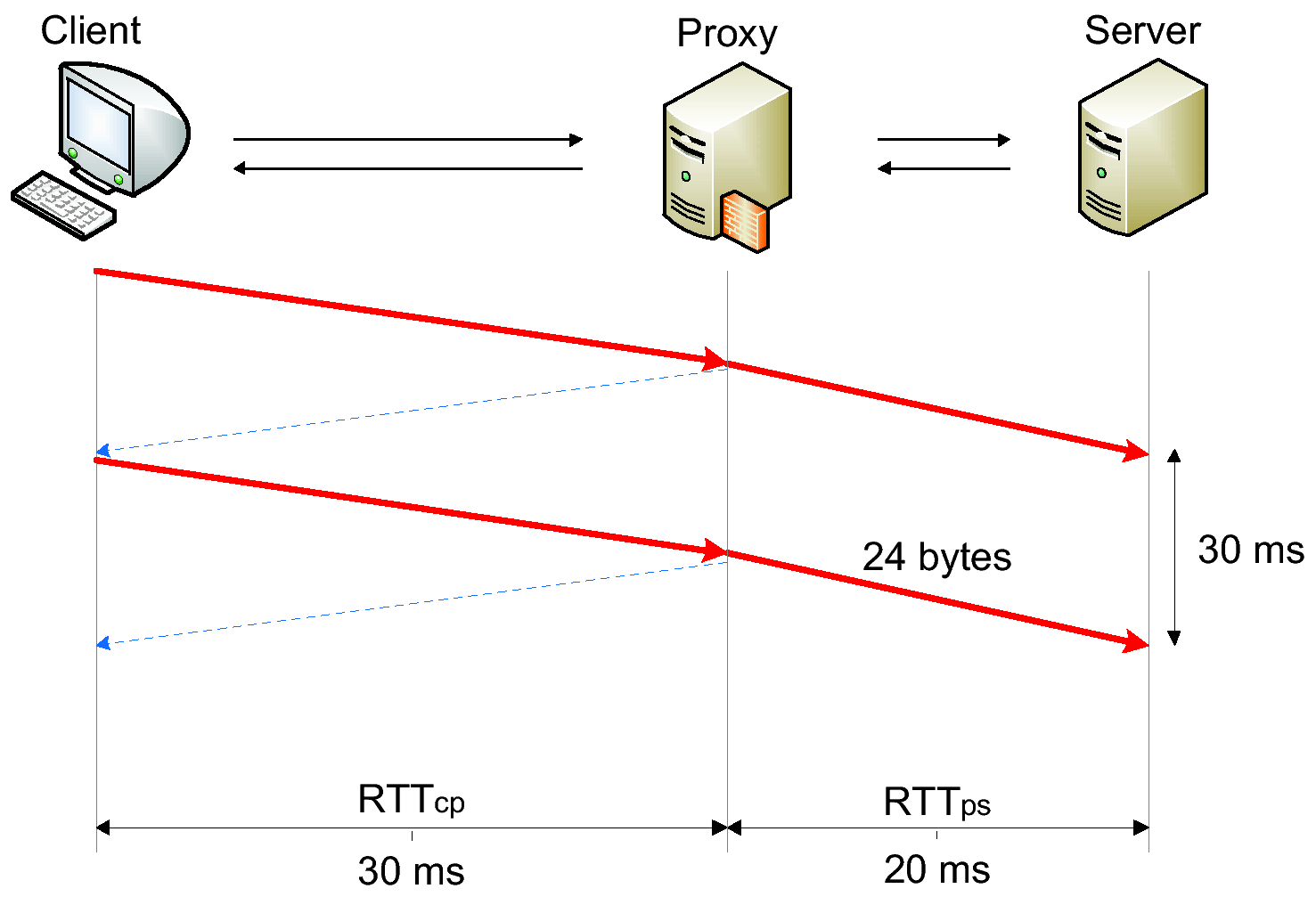 (b) Nagle-disabled proxy with RTTcp > RTTps
(b) Nagle-disabled proxy with RTTcp > RTTps
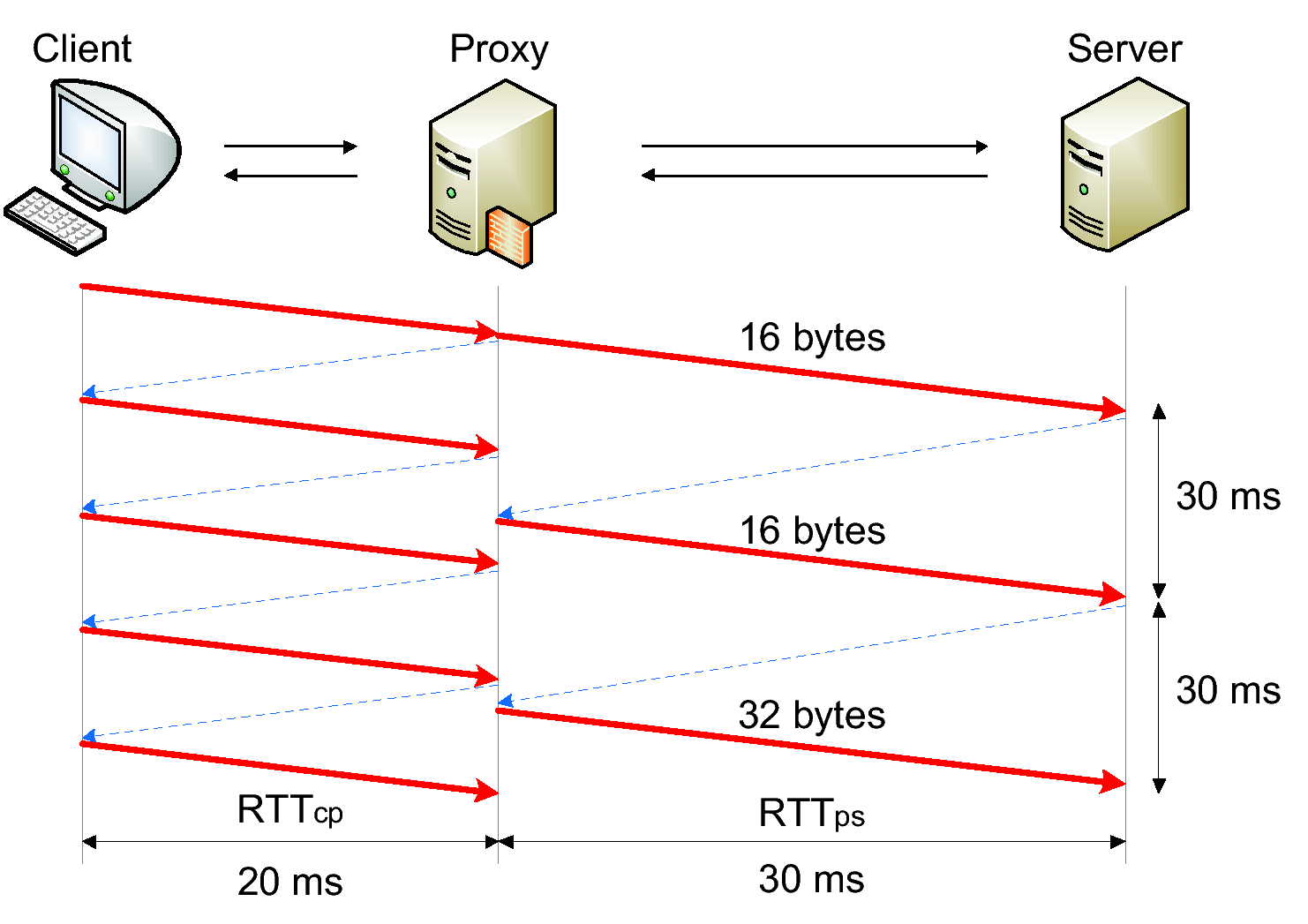 (c) Nagle-enabled proxy with RTTcp < RTTps
(c) Nagle-enabled proxy with RTTcp < RTTps
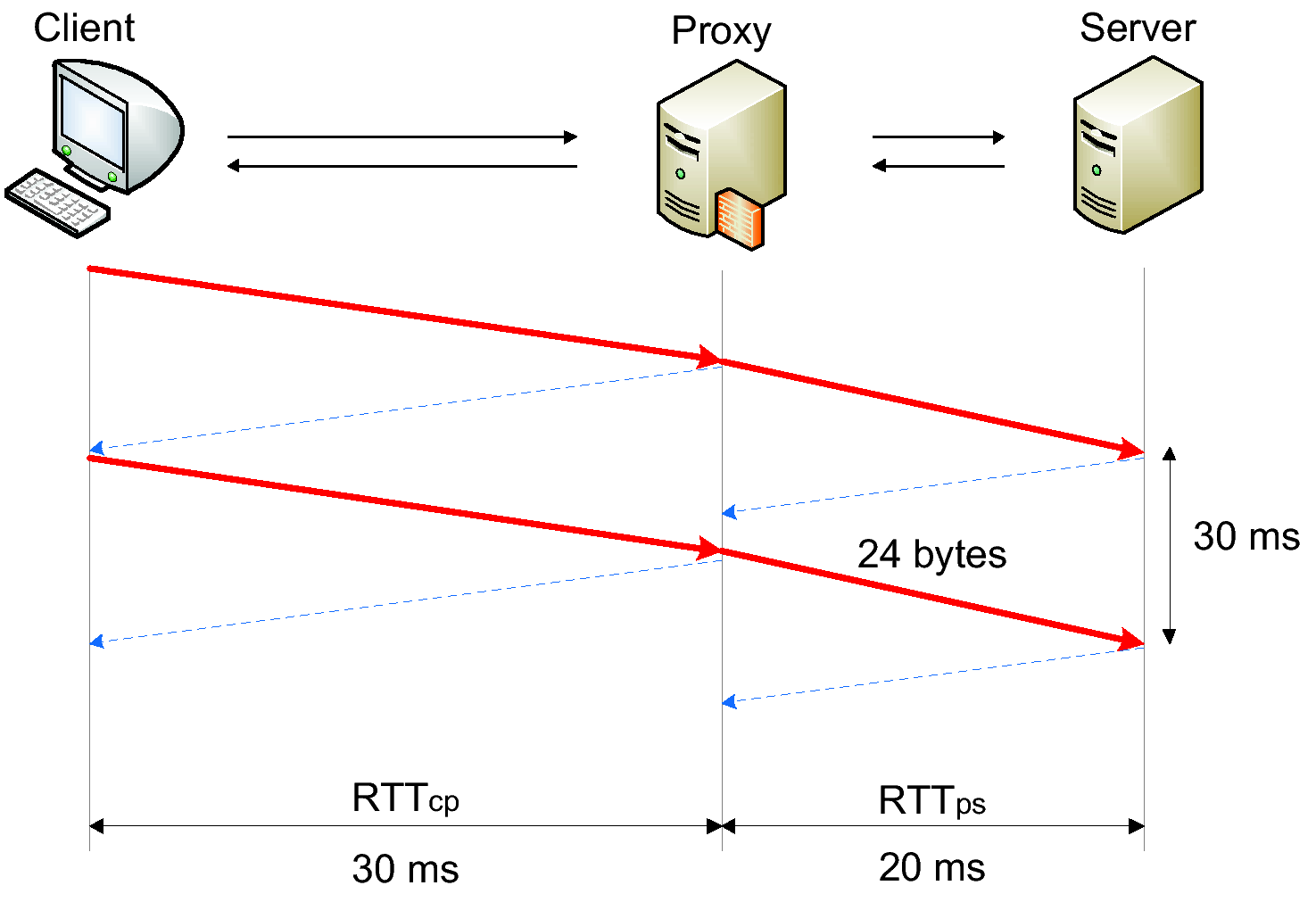 (d) Nagle-enabled proxy with RTTcp > RTTps
(d) Nagle-enabled proxy with RTTcp > RTTps