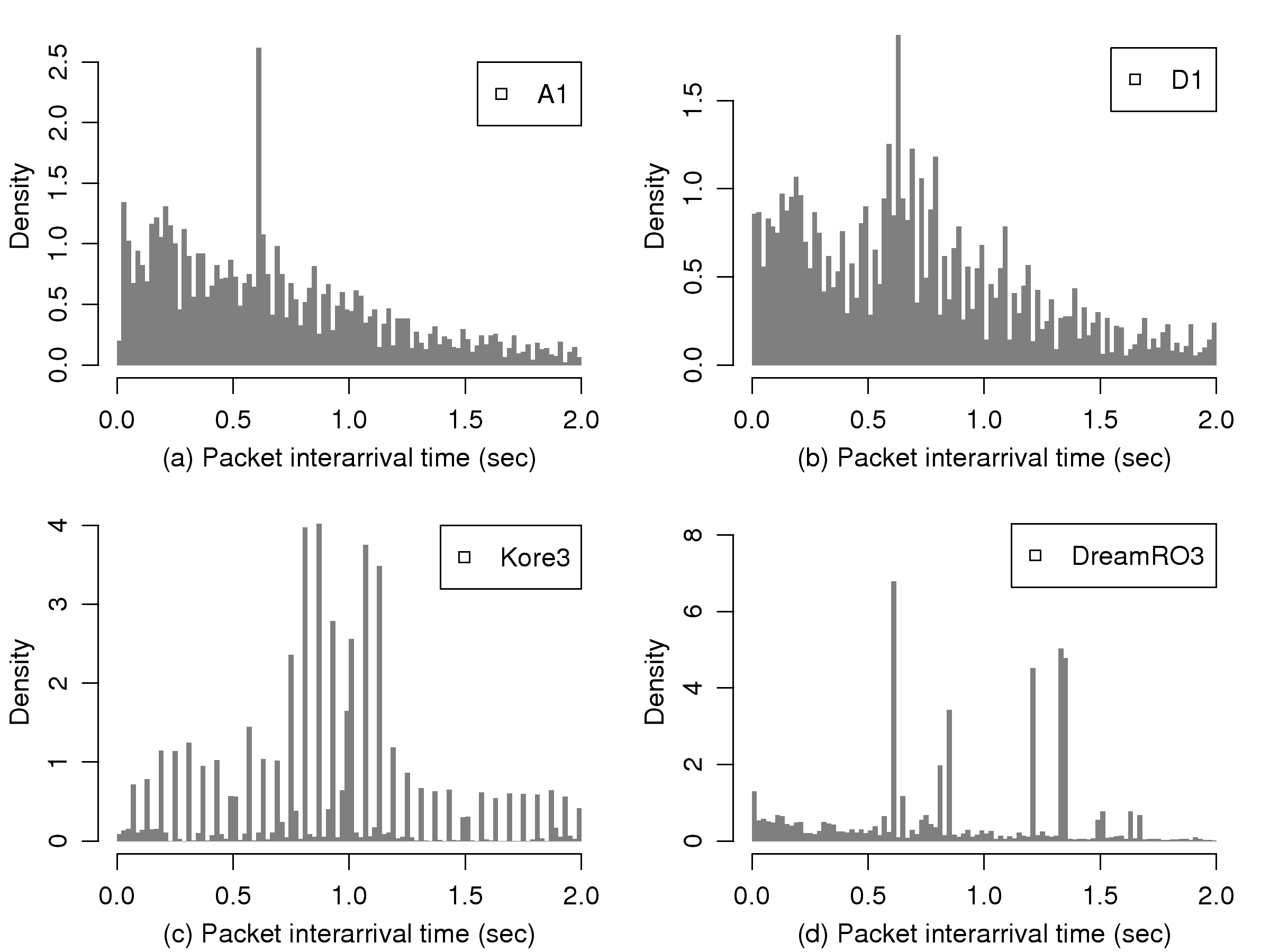
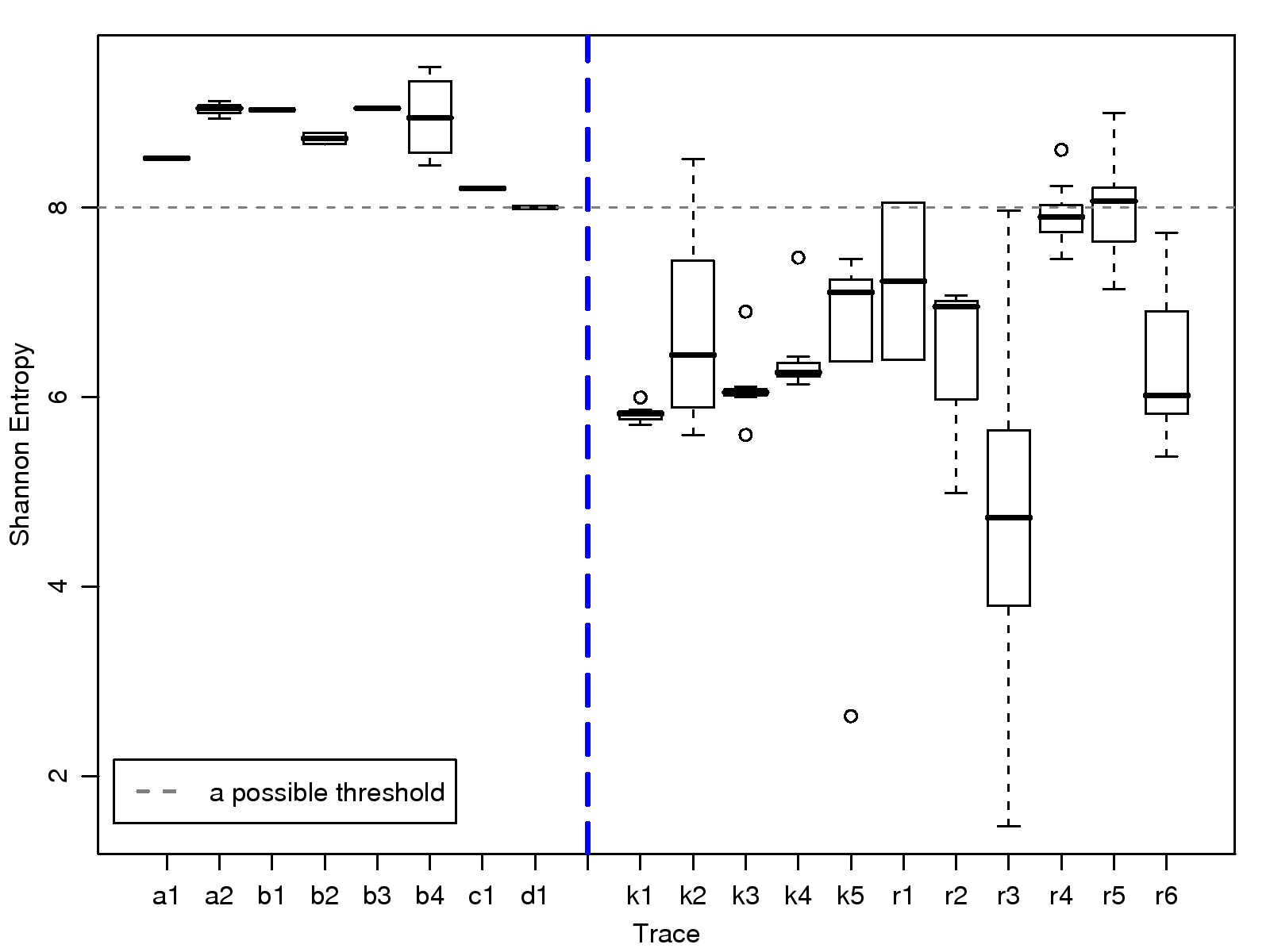
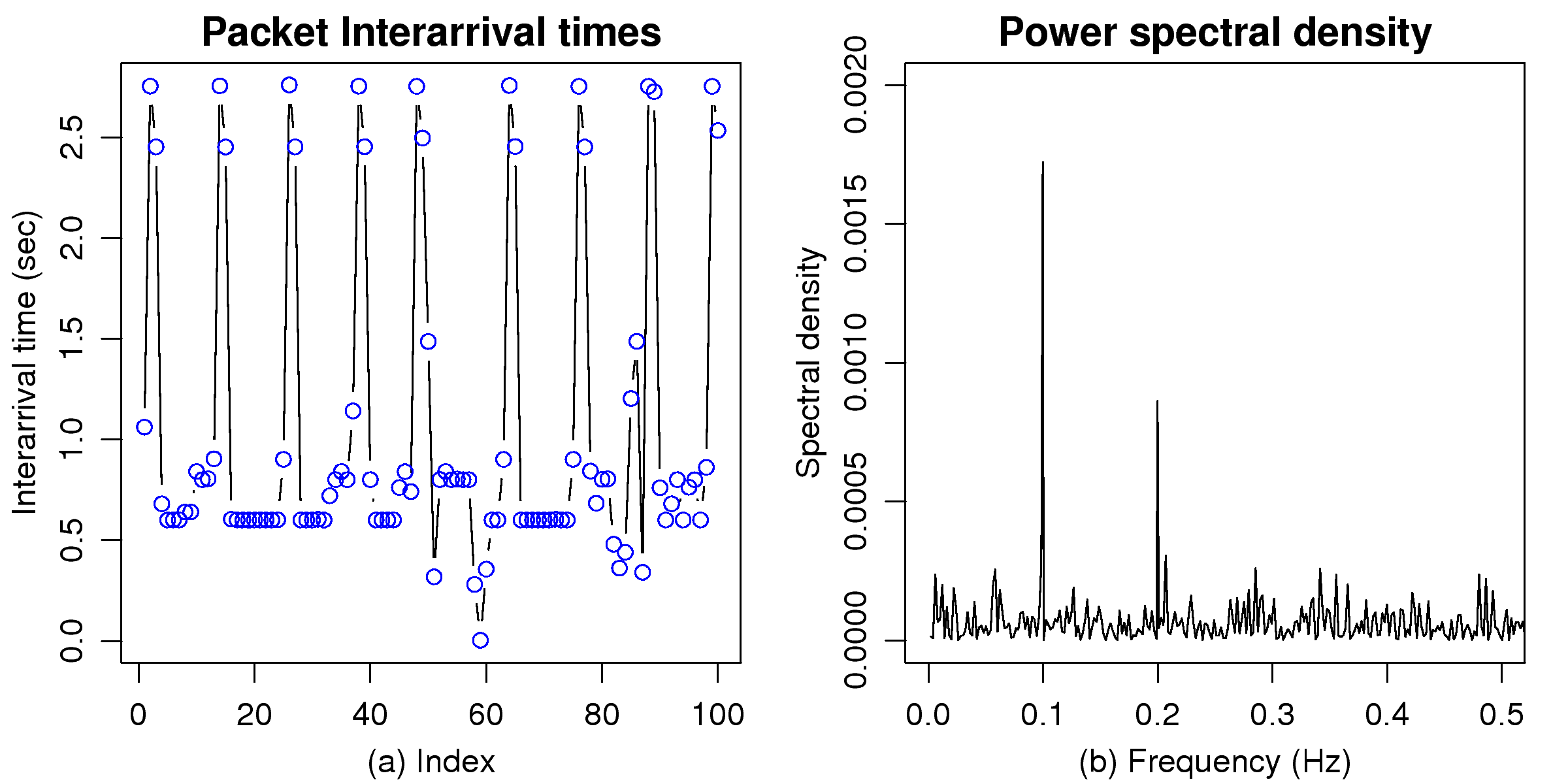
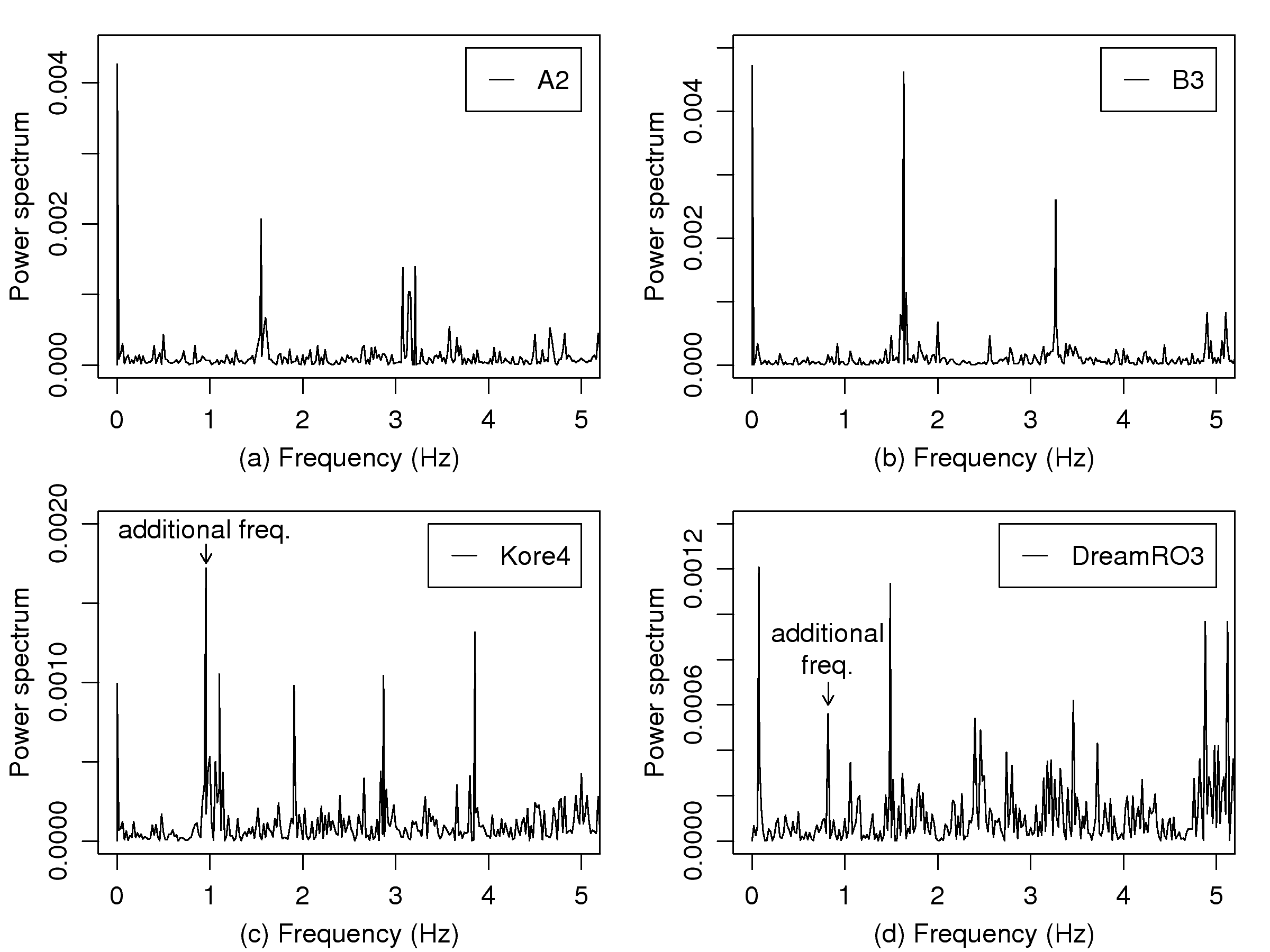
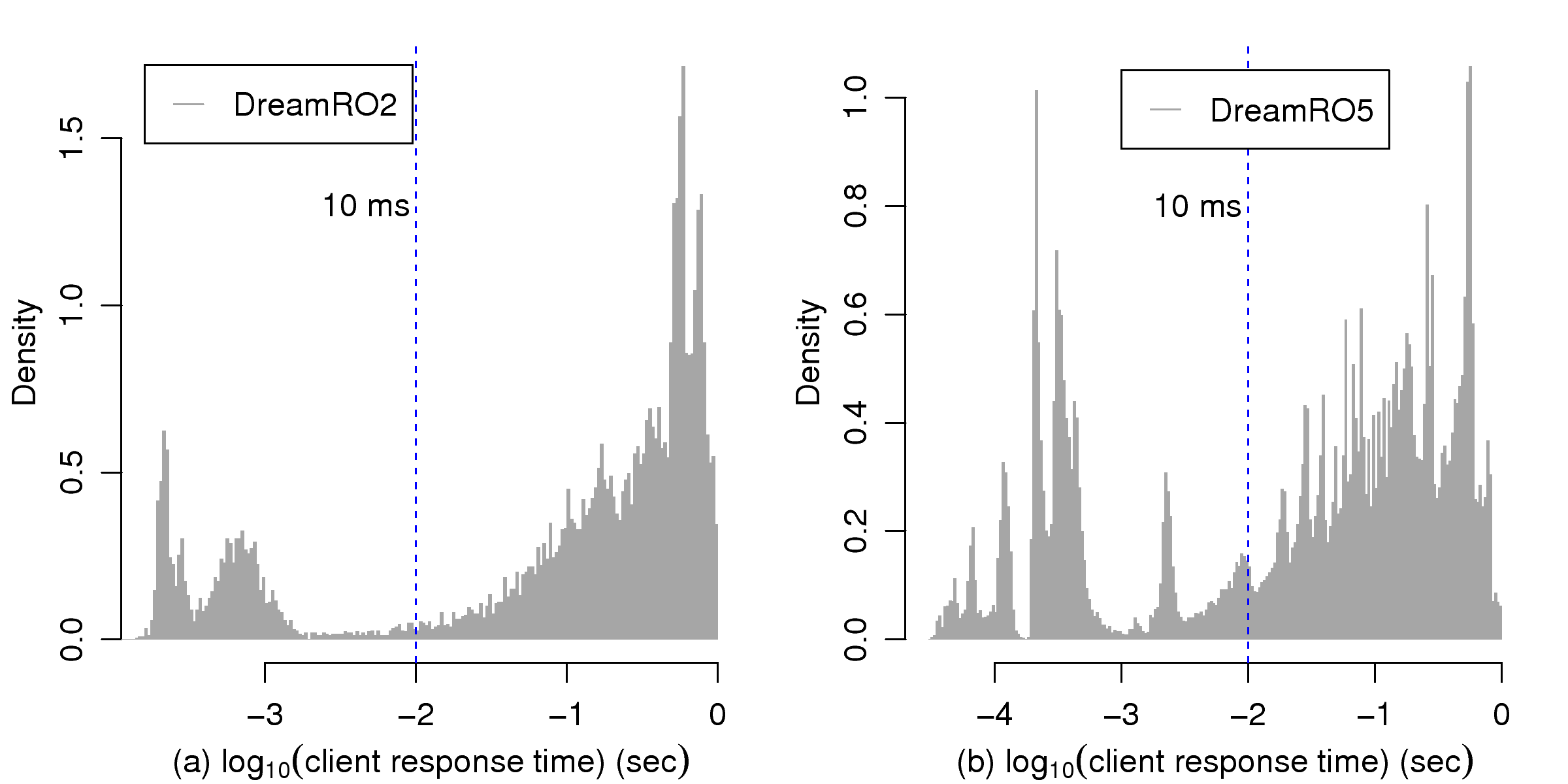
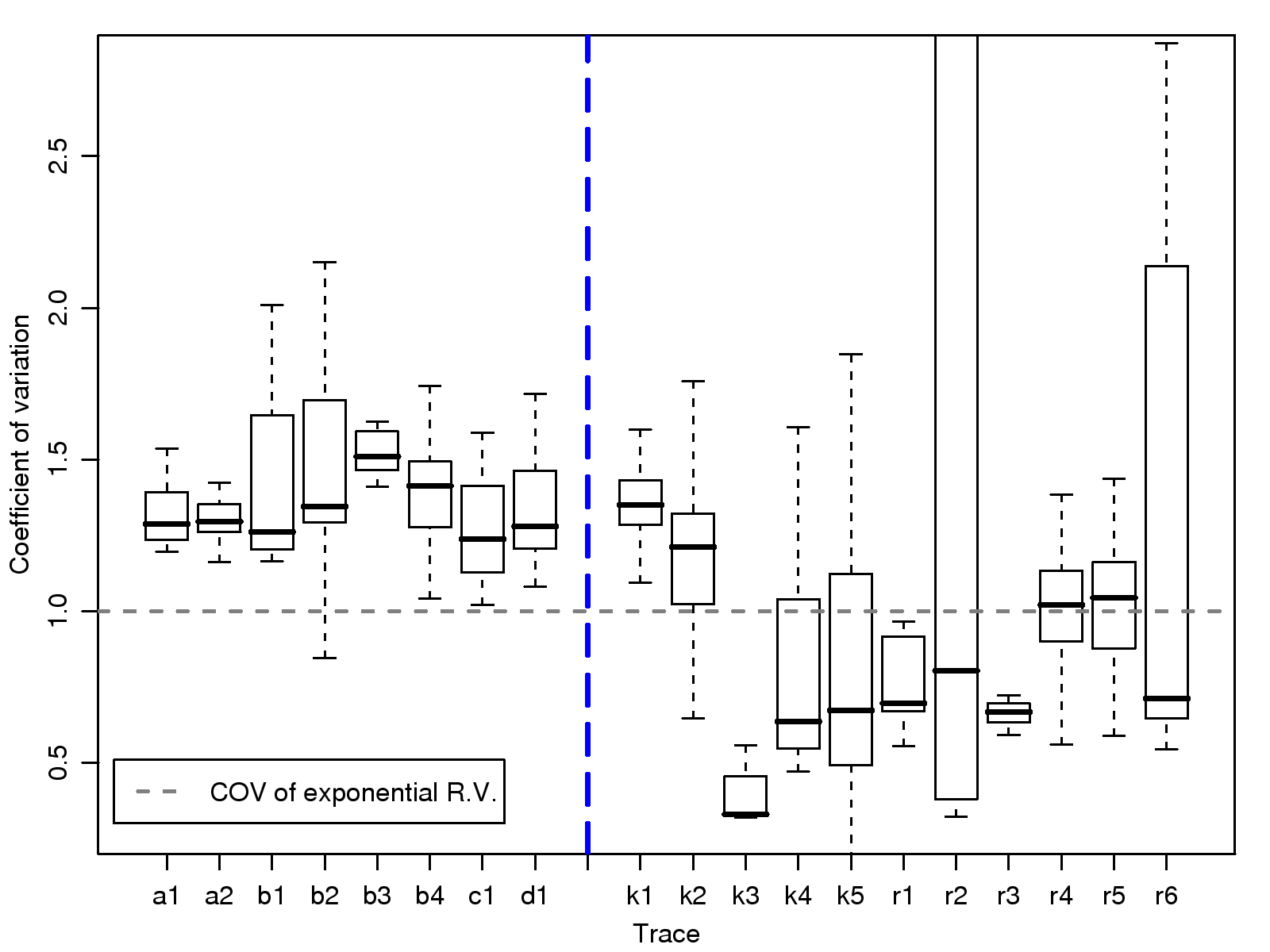
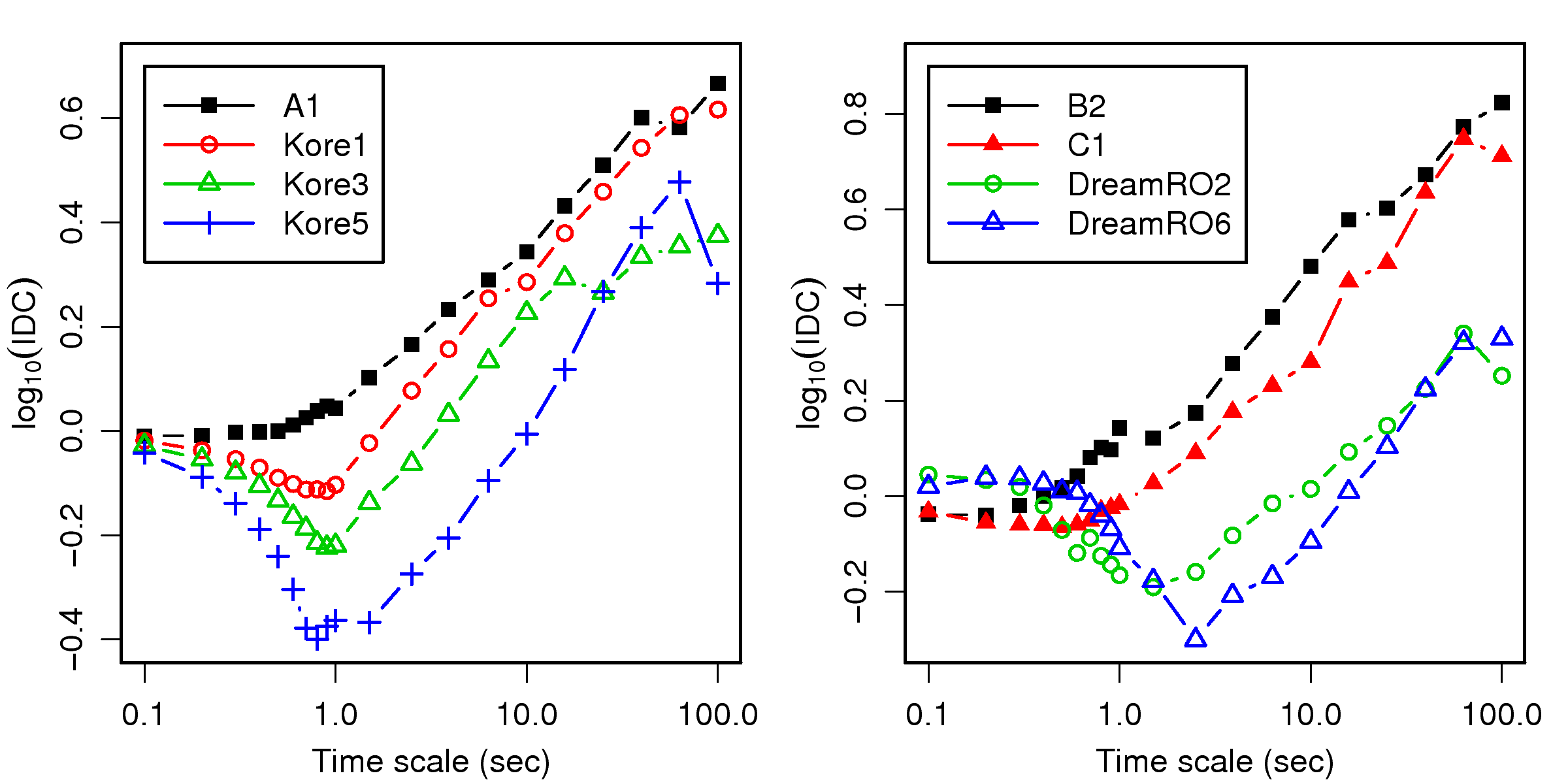
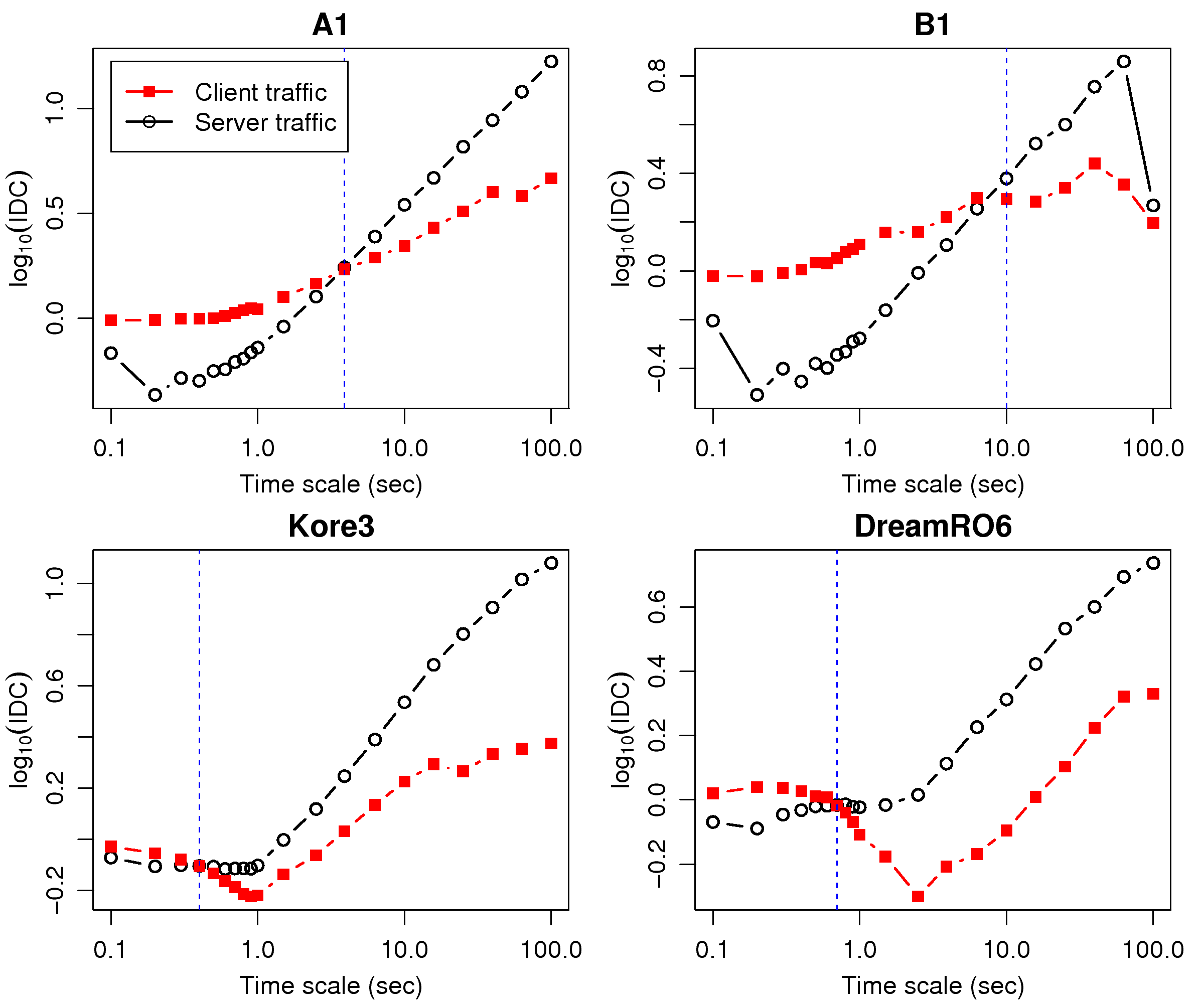
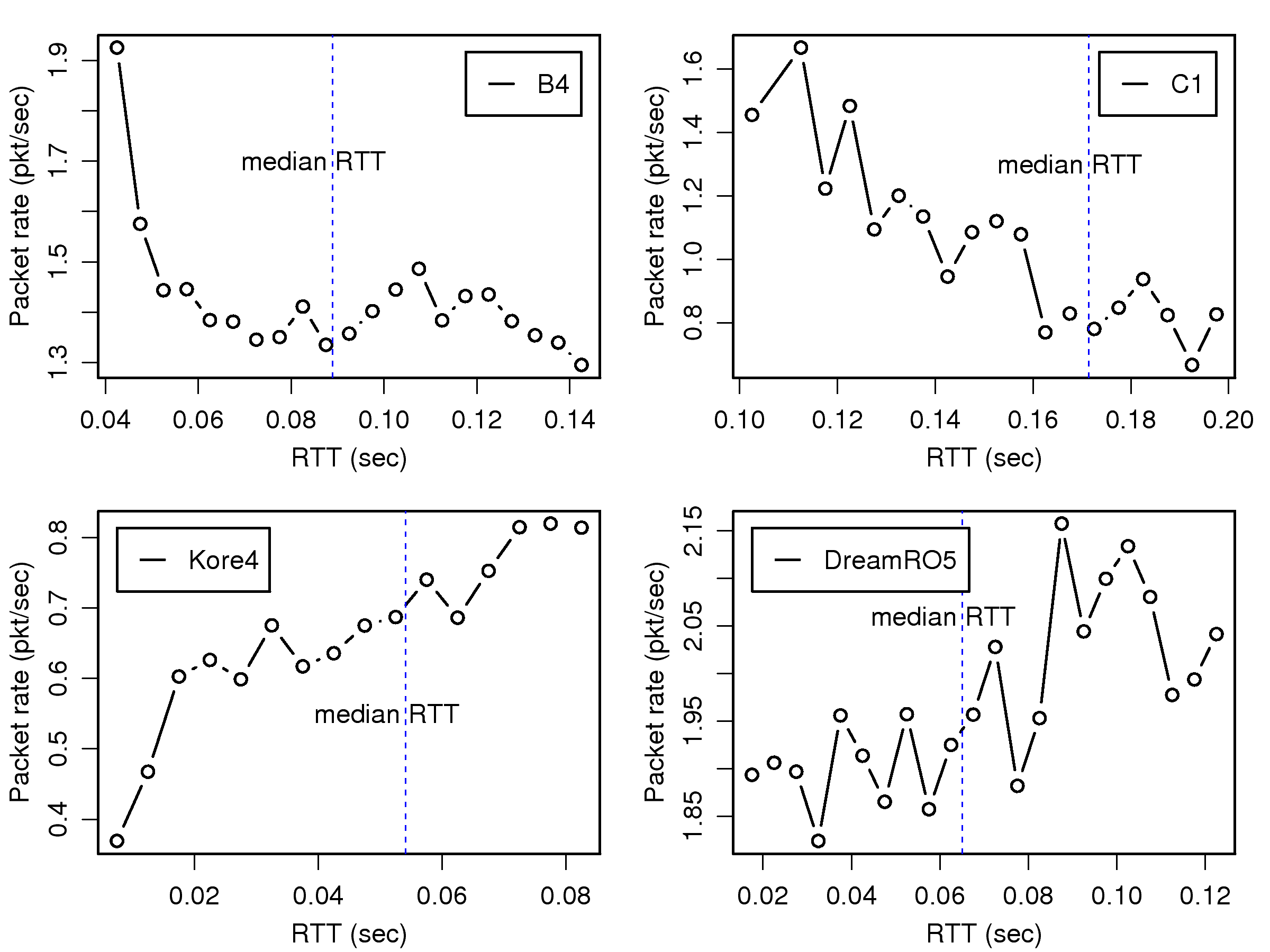
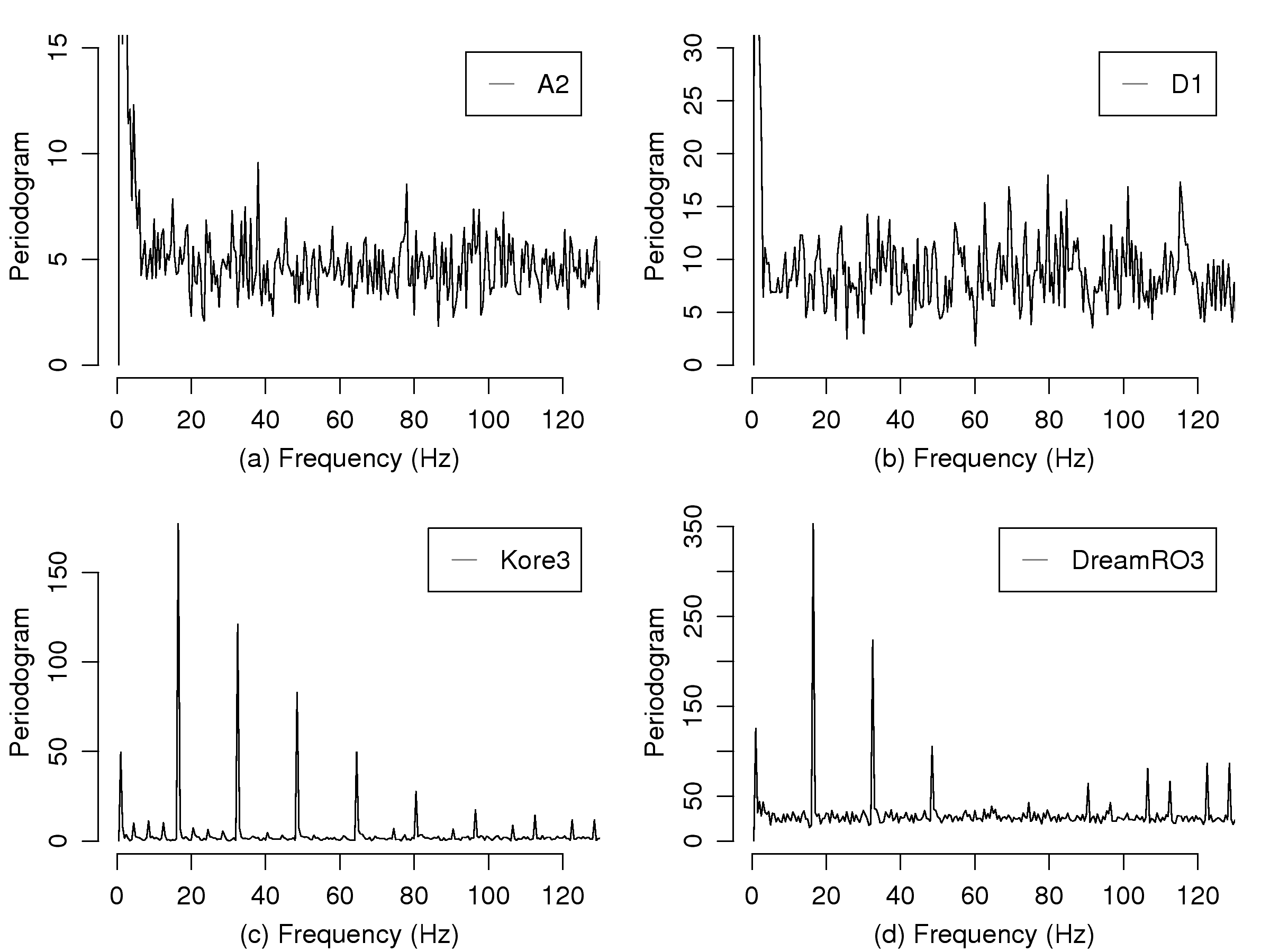
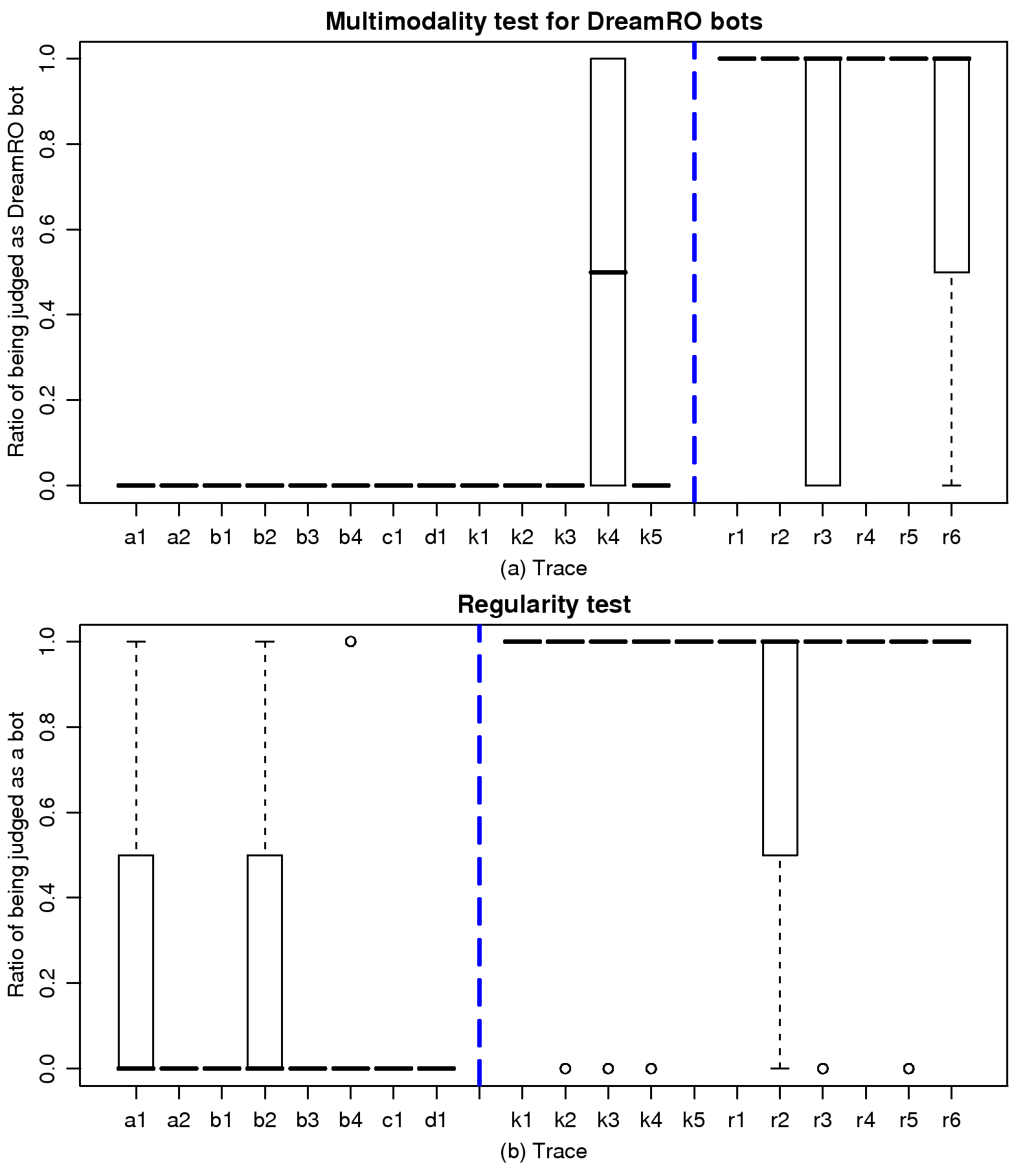
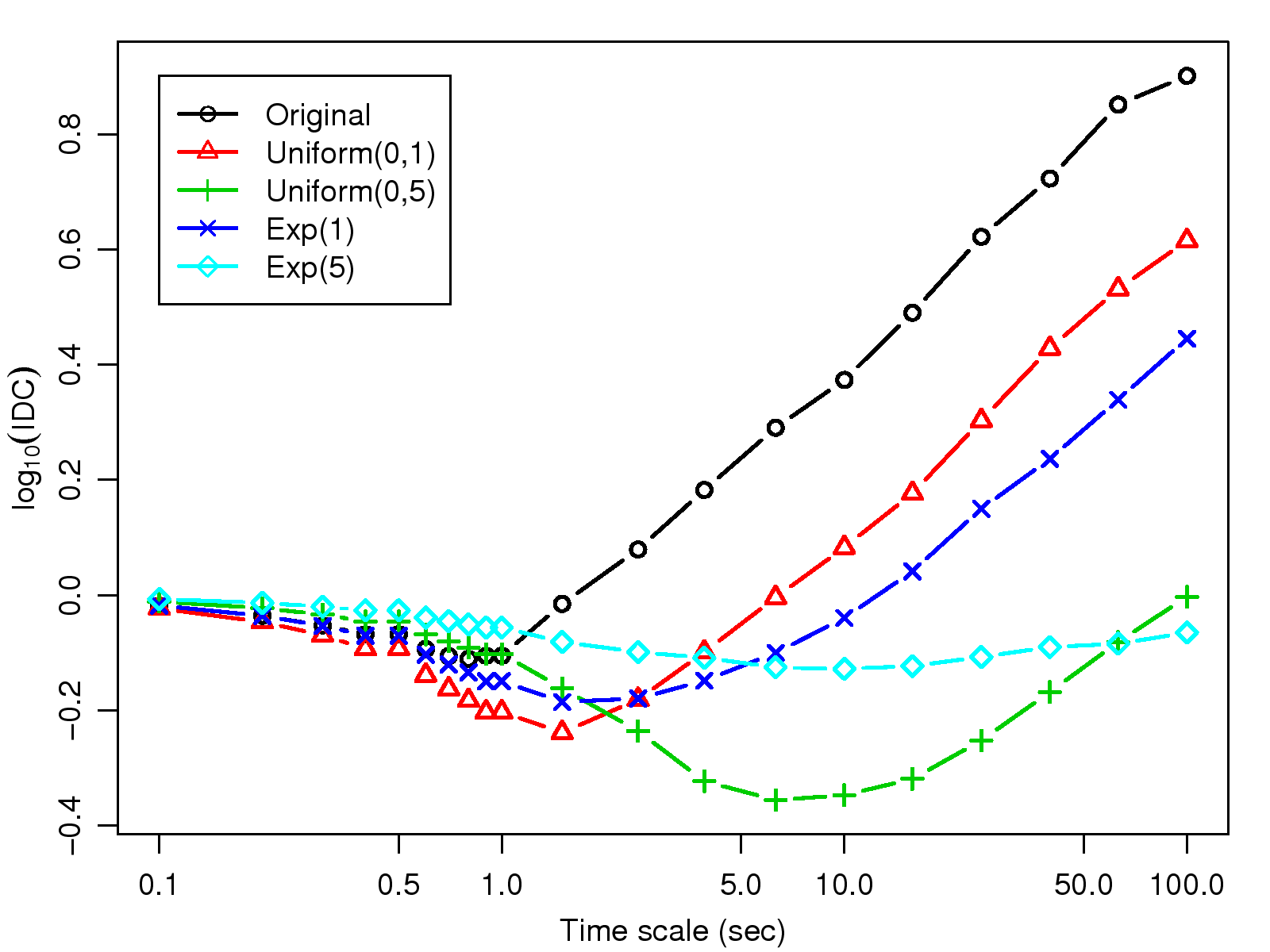
[1]
N. E. Baughman and B. N. Levine, "Cheat-proof playout for centralized and
distributed online games," in
Proceedings of IEEE INFOCOM 2001,
Anchorage, AK, Apr. 2001.
[2]
P. Bloomfield,
Fourier Analysis of Time Series: An Introduction. New York: John Wiley & Sons, 2000.
[3]
K.-T. Chen, P. Huang, and C.-L. Lei, "
Game Traffic Analysis: An MMORPG Perspective,"
Computer Networks, vol. 50, no. 16, 2006.
[4]
--, "
How Sensitive are Online Gamers to Network Quality??"
Communications of the ACM, vol. 49, no. 11, pp. 34-38, Nov 2006.
[5]
K.-T. Chen, A. Liao, H.-K. K. Pao, and H.-H. Chu, "
Game Bot Detection Based on Avatar Trajectory," in
Proceedings of IFIP ICEC 2008, 2008.
[6]
K.-T. Chen, H.-K. K. Pao, and H.-C. Chang, "
Game Bot Identification based on Manifold Learning," in
Proceedings of ACM NetGames 2008, 2008.
[7]
E. Cronin, B. Filstrup, and S. Jamin, "Cheat-proofing dead reckoned
multiplayer games," in
Proc. of 2nd International Conference on
Application and Development of Computer Games, Jan 2003.
[8]
R. Dechter and J. Pearl, "Generalized best-first search strategies and the
optimality of a*,"
J. ACM, vol. 32, no. 3, pp. 505-536, 1985.
[9]
M. DeLap, B. Knutsson, H. Lu, O. Sokolsky, U. Sammapun, I. Lee, and
C. Tsarouchis, "Is runtime verification applicable to cheat detection?" in
Proceedings of ACM SIGCOMM 2004 workshops on NetGames '04. ACM Press, 2004, pp. 134-138.
[10]
C. Dellarocas, "The digitization of word of mouth: Promise and challenges of
online feedback mechanisms,"
Manage. Sci., vol. 49, no. 10, pp.
1407-1424, 2003.
[11]
R. A. Fisher, "Tests of significance in harmonic analysis,"
J. Roy.
Stat. Soc., Ser. A, vol. 125, pp. 54-49, 1929.
[12]
W. A. Fuller,
Introduction to statistical time series. John Wiley & Sons, 1996.
[13]
P. Golle and N. Ducheneaut, "Preventing bots from playing online games,"
Computers in Entertainment, vol. 3, no. 3, pp. 3-3, 2005.
[14]
B. Gorman and M. Humphrys, "Towards integrated imitation of strategic planning
and motion modeling in interactive computer games,"
Computers in
Entertainment, vol. 4, no. 4, p. 10, 2006.
[15]
R. Gusella, "Characterizing the variability of arrival processes with indexes
of dispersion,"
IEEE J. Select. Areas Commun., vol. 9, no. 2, Feb.
1991.
[16]
--, "A characterization of the variability of packet arrival processes in
workstation networks," Ph.D. dissertation, University of California at
Berkeley, 1990.
[17]
J. Hartigan and P. Hartigan, "The dip test of unimodality,"
Ann.
Stat., vol. 13, pp. 70-84, 1985.
[18]
P. M. Hartigan, "Computation of the dip statistic to test for unimodality,"
Appl. Stat., vol. 34, no. 3, pp. 320-325, Sep. 1985.
[19]
M. Kendall, "A new measure of rank correlation,"
Biometrika, vol. 30,
pp. 81-93, 1938.
[20]
H. Kim, S. Hong, and J. Kim, "Detection of auto programs for MMORPGs," in
Proceedings of AI 2005: Advances in Artificial Intelligence, 2005, pp.
1281-1284.
[21]
L. von Ahn, M. Blum, N. J. Hopper, and J. Langford, "CAPTCHA: Using hard
AI problems for security," in
Proceedings of Eurocrypt, 2003, pp.
294-311.
[22]
B. S. Woodcock, "An analysis of MMOG subscription growth - version 21.0,"
http://www.mmogchart.com/. [Online]. Available:
http://www.mmogchart.com/
[23]
J. Yan and B. Randell, "A systematic classification of cheating in online
games," in
Proceedings of ACM SIGCOMM 2005 workshops on NetGames
'05. ACM Press, 2005.
[24]
S. Yeung, J. C. Lui, J. Liu, and J. Yan, "Detecting cheaters for multiplayer
games: Theory, design and implementation," in
Proceedings of IEEE
International Workshop on Networking Issues in Multimedia Entertainment
(NIME'06), Las Vegas, USA, Jan 2006.